UK US ISRAEL NSA Likely Creators of the New Stuxnet Regin Malware
The Israeli Criminals Behind the NSA Spy Scandal
www.bollyn.com/the-israeli-criminals-behind-the-nsa-spy-scandal/
Jun 13, 2013 - At the center of the NSA scandal is a gang of Israeli high-tech criminals .... Shortly after 9-11, Odigo was completely taken over by Comverse ...Comverse were closely connected to Odigo, the Israeli messaging system that was used to warnIsraelis to stay away from the World Trade Center on 9-11...Kobi Alexander is also closely connected to the 9-11 criminal atrocity. ... with securities, mail and wire fraud by U.S. prosecutors in Brooklyn, New York.- .
Nir Zuk's Palo Alto Networks Is Blowing Up Internet Security
www.forbes.com/.../nir-zuks-palo-alto-networks-is-blowing-up-int...ForbesMar 27, 2013 - Palo Alto Networks founder and CTO Nir Zuk. ... The Israeli engineer felt his best ideas were being blocked by incompetence and office politics. .... Zuk served in the IDF through 1994, spending an extra year in officer training, ...How I Got Here: Nir Zuk, CTO, Palo Alto Networks | ITworld
www.itworld.com/.../how-i-got-here--nir-zuk--cto--palo-alto-networks.ht...Apr 5, 2010 - Nir Zuk, founder and CTO of Palo Alto Networks, is passionate about ... Starting as a 16-year-old whiz kid in Israel, writing some of the very first ...
9/11,Israeli Nir Zuk,NSA,Unit 8200,Palo Alto Networks,Google
wolfblitzzer0.blogspot.com/.../israeli-nir-zuknsaunit-8200palo-alto.html
9/11,Mossad Unit 8200:Israeli Terrorists In Control Of NSA ...
wolfblitzzer0.blogspot.com/.../911israeli-terrorists-in-control-of-nsa.html
9/11,Israeli Nir Zuk,NSA,Unit 8200,Palo Alto Networks,Google
wolfblitzzer0.blogspot.com/.../israeli-nir-zuknsaunit-8200palo-alto.html
Dec 15, 2013 - Nir Zuk's Palo Alto Networks Is Blowing Up Internet Security - Forbes. www.forbes.com/. .... wolfblitzzer0: SEC,9/11:Israel IDF,NSA Snooping Technology 'Start . ..... NSA,Diane Feinstein:Room 641A, 611 Folsom Street S.. New Questions Raised About NSA-Israel Intelligence Sharing
www.commondreams.org/.../new-question...
Common Dreams NewsCenterSep 18, 2014 - Recently reported comments made by NSA whistleblower Edward Snowden about the U.S. government's intelligence-sharing practices with ...NSA Has 'Far-Reaching' Partnership With Israeli Intelligence ...
www.huffingtonpost.com/.../nsa-partnership-israel_...
The Huffington PostAug 4, 2014 - Several of the documents published center on the assistance the NSAprovides to the Israeli SIGINT National Unit, the secretive signals ...NSA hands Israel intelligence data on 'US persons' - CNET
www.cnet.com/.../nsa-hands-israel-intelligence-data-on-us-persons/
CNETWhistleblower Edward Snowden leaks a new document that outlines the NSA'swidespread sharing of raw metadata with Israeli security agencies.
Palo Alto Networks buys ex-NSA founded startup Morta ...
www.zdnet.com/palo-alto-networks-buys-ex-nsa-founded-startup-...
ZDNetJan 6, 2014 - Palo Alto Networks has acquired Morta Security, a Silicon Valley startup run by former U.S. Air Force and National Security Agency (NSA) staff.
Regin: Giving IT security reason to hope NSA is waaaay ahead on ...
Computerworld-7 hours ago
Security pros don't need screaming headlines to put them on alert about a dangerous new piece of malware. "New" and "present" are usually ...
This Malware May Have Gotten the NSA Caught With Its Hand in the ...
Foreign Policy (blog)-5 hours ago
Foreign Policy (blog)-5 hours ago
Secret Malware in European Union Attack Linked to US and British ...
Highly Cited-The Intercept - First Look Media-10 hours ago
Highly Cited-The Intercept - First Look Media-10 hours ago
Symantec Discovers 'Regin' Spy Code Lurking on Computer Networks
Blog-New York Times (blog)-5 hours ago
Blog-New York Times (blog)-5 hours ago
NSA ISRAELI SPYS AND STOCK TOUTERS OF PALO ALTO NETWORKS
Startup Fights Fraud With Tools From Facebook and the NSA
Both Facebook and the NSA, you see, have open sourced their software, ..... Palo Alto Networks share price has increased more than 140 ...
Palo Alto Networks buys ex-NSA founded startup Morta Security
Palo Alto Networks has acquired Morta Security, a Silicon Valley startup run by former U.S. Air Force and National Security Agency (NSA) staff.
Apple Says It's Blocking a New Strain of Malware Infecting Macs and ...
On Wednesday, Palo Alto Networks, a cybersecurity firm in Silicon Valley, ... “An NSA or GCHQ, or any other sophisticated attacker could easily ...
http://www.ibtimes.co.uk/regin-malware-uk-us-israel-likely-creators-new-stuxnet-1476358
Regin Malware: UK, US or Israel Likely Creators of the New Stuxnet
-
November 24, 2014 16:26 GMT

A sophisticated piece of malware which has been compared in complexity to Stuxnet or Duqu, Regin has targeted victims in Russia, Saudi Arabia, Ireland and Mexico.
More information has been published about the sophisticated Regin malware, as western powers are fingered as the most obvious creators.
The first details about the Regin malware were published by Symantec detailing a highly targeted attack which was capable of taking control of systems to spy on government organisations, businesses and private individuals. The security company failed to identify where Regin originated from, saying only that it looked like the work of a nation-state.
As more details about the complex computer code begin to emerge, some prominent security experts have said the most likely suspects are the UK, US or Israel.
Speaking to the Guardian, Mikko Hypponen from F-Secure ruled out China and Russia as the creators of Regin: "We believe Regin is not coming from the usual suspects. We don't think Regin was made by Russia or China."
As reporter Tom Brewster-Fox points out, this only really leaves the US, UK or Israel as the countries with the technical know-how to create a piece of malware as sophisticated as Regin.
Another F-Secure expert, Sean Sullivan, responded to this assumption saying: "That is a very astute observation on your part...there are no other countries I can think of."
Hopscotch, Legspin, Starbucks and S**t
Symantec reported that the majority of infections were found in Russia and Saudi Arabia, with Ireland and Mexico next on the list, though the attacks are highly targeted, with Kaspersky's researchsuggesting there are only 100 victims found so far, since the malware first surfaced in 2008.
According to new details published by Kaspersky Lab, which has been tracking Regin since 2012, there is further evidence to back up claims this malware was written by English-speaking authors.
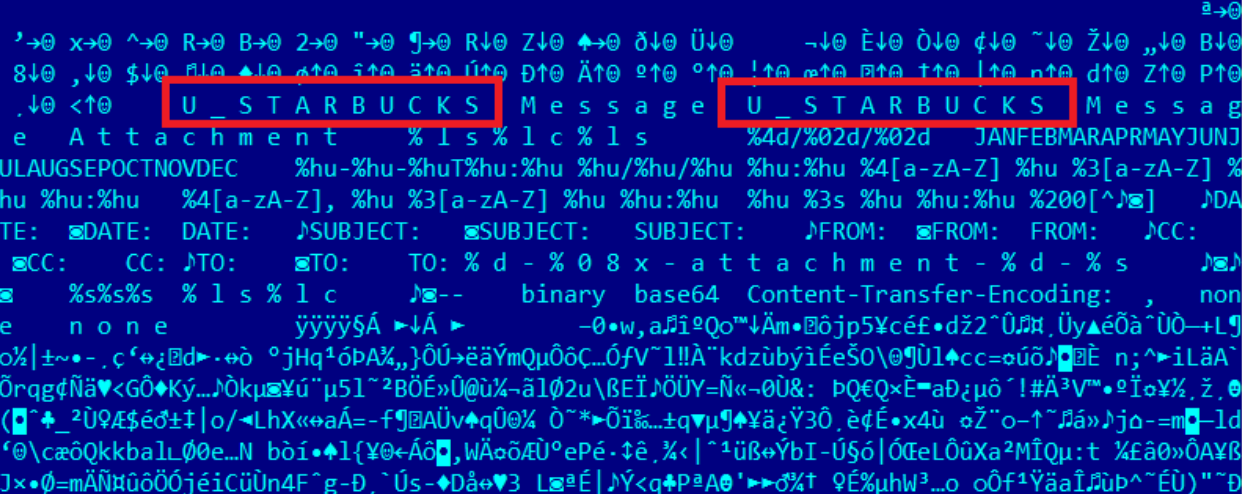
Mention of Starbucks in the Regin code could indicate it was created in the US(Kaspersky Labs)
Within the virtual file system of Regin, Kaspersky Lab researchers found the words "legspin", "hopscotch", "Starbucks" and "s**t" which could suggest a collaboration between the US and the UK given the origin of these words.
The research from Kaspersky Lab revealed an additional feature of Regin, showing that the sophisticated piece of malware is capable of manipulating GSM networks allowing them take control of the phone on the network.
"In today's world, we have become too dependent on mobile phone networks which rely on ancient communication protocols with little or no security available for the end user," said Costin Raiu, Director of Global Research and Analysis Team at Kaspersky Lab.
"Although all GSM networks have mechanisms embedded which allow entities such as law enforcement to track suspects, other parties can hijack this ability and abuse it to launch different attacks against mobile users."
Kaspersky Lab revealed that the people behind Regin were able to infect one major operator in the Middle East, giving them "access to information about which calls are processed by a particular cell, redirect these calls to other cells, activate neighbour cells and perform other offensive activities," Kaspersky Lab researchers wrote. "At the present time, the attackers behind Regin are the only ones known to have been capable of doing such operations."

No comments:
Post a Comment